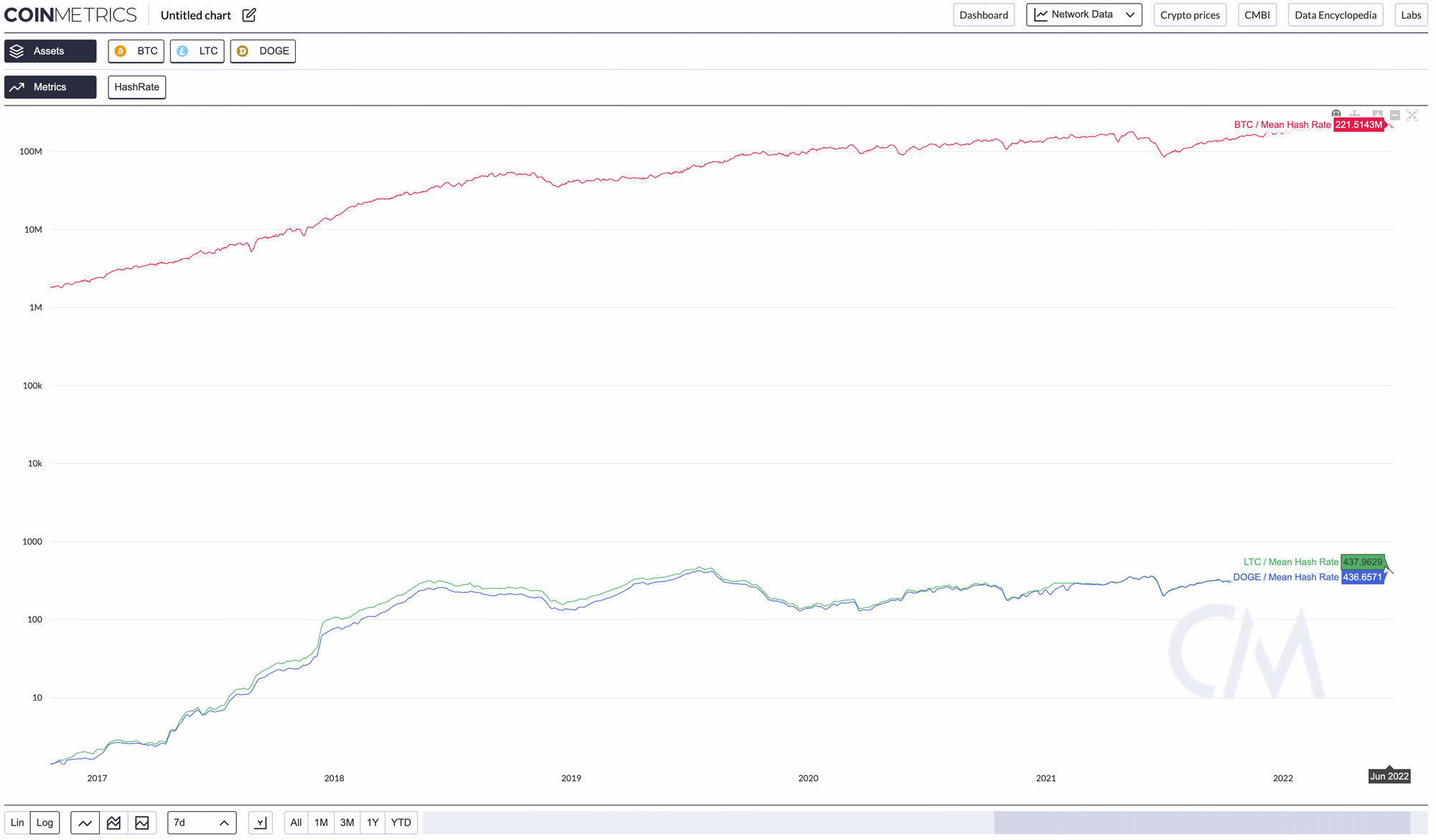
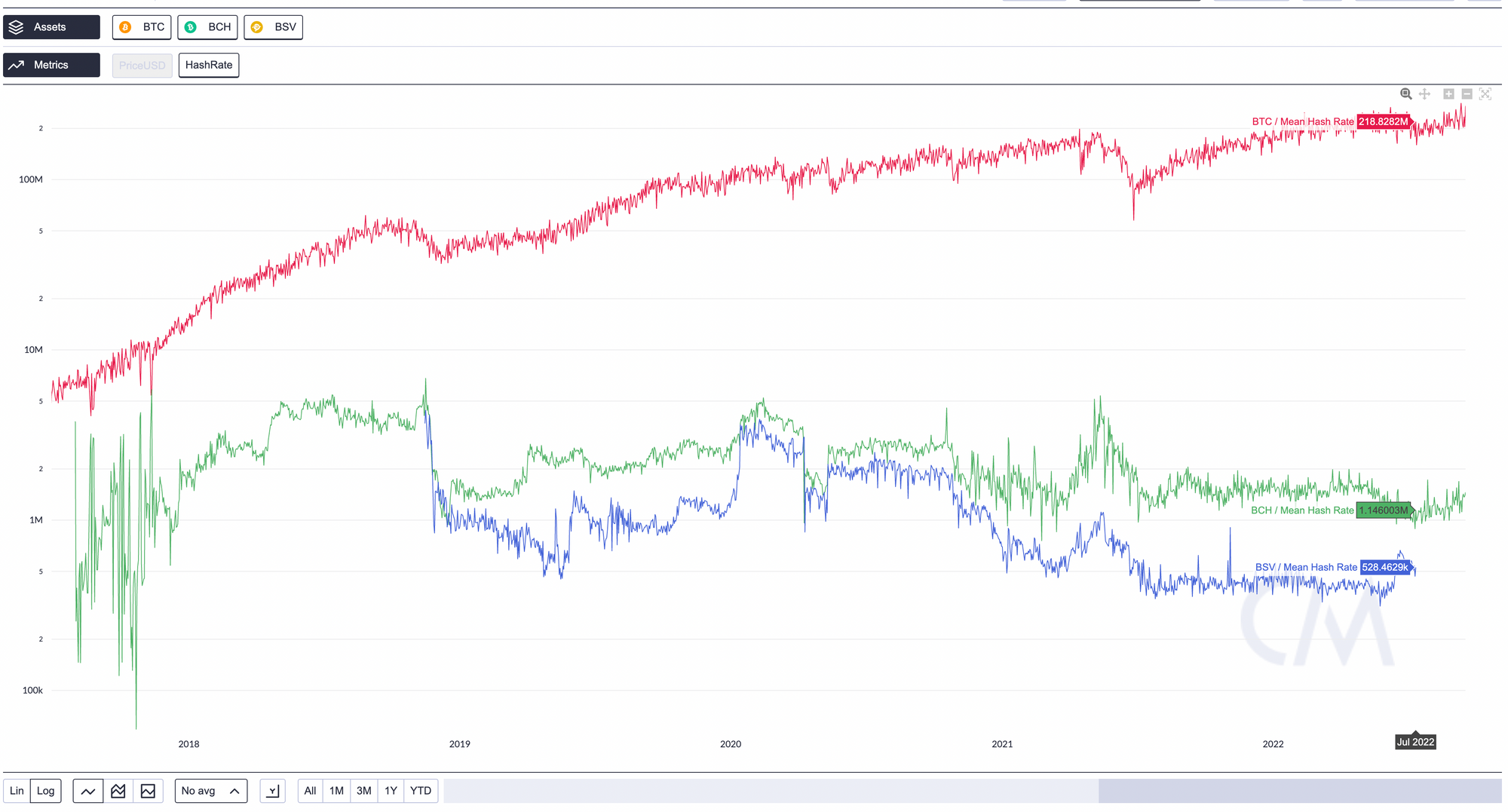
SHA256 vs Scrypt: Why Comparing Hash Rates of Different Hashing Algorithms is Misleading
Application Specific Integrated Circut (ASIC) miners are designed to mine a specific algorithm; they cannot be configured to mine a different algorithm.
It is not an apples-to-apples comparison.
SHA-256 and Scrypt are not physical fruits, they are mathematical functions, and it's not appropriate to compare them to any physical fruit. They are mathematical algorithms that are used to perform specific tasks, in this case, to hash and secure data in a unique way. They have specific properties, characteristics, and behaviors that are unique to them and are important to understand in the context of cryptography and blockchain technology.
Comparing the hashrate of SHA-256 and Scrypt is like comparing apples to oranges. SHA-256 and Scrypt are both cryptographic hash functions just like how apples and oranges are fruits, but they have different nutritional values, tastes, and origins. SHA256 is computationally-intensive, while Scrypt is designed to be computationally and memory-intensive.
In this article you will learn why it is impossible to make apple juice from oranges.
What is SHA-256?
SHA-256 is a cryptographic hash function widely used for various applications, including Bitcoin mining. It is used in Bitcoin's Proof-of-Work consensus mechanism. It is considered more secure than many other hash functions because it is less vulnerable to certain types of attacks, such as collision attacks and preimage attacks.
The reason why SHA-256 is a computationally-intensive algorithm is the mathematical operations it performs. It applies a series of bitwise operations and logical functions (such as AND, OR, NOT, and XOR) to the input data in a specific order, requiring many CPU cycles to complete. The algorithm operations are designed to consume significant time and resources, making it computationally expensive to execute.
What is Scrypt?
Scrypt (pronounced "ess crypt") is a cryptographic memory-hard hash function created by Colin Percival and was specifically designed to be more memory-intensive than computationally-intensive, meaning that its computation requires a large amount of memory and relatively less CPU power. This is done to make it difficult for an attacker to perform a precomputation attack and to reduce the advantage of using specialized hardware (such as an ASIC) to accelerate the hash computations.
The reason why Scrypt is a memory-intensive algorithm is its use of a large "memory-hard" buffer. The algorithm uses a buffer of size 2^n where n is a parameter the user can choose. This memory buffer is filled with random data, and the algorithm repeatedly makes memory-access operations at random locations in the memory buffer to perform mathematical operations on the data.
Are SHA-256 ASIC miners capable of attacking blockchains that use the Scrypt algorithm, such as Litecoin and Dogecoin?
SHA-256 ASIC miners are specialized hardware devices specifically designed to efficiently mine SHA-256 algorithms, such as the ones used in Bitcoin mining. These devices cannot mine Scrypt algorithms, such as the ones used in Litecoin and Dogecoin, because they are optimized for the SHA-256 algorithm and would be less efficient at mining Scrypt. It would be uneconomical as it would be more profitable for them to mine Bitcoin.
ASICs are designed to perform specific calculations and operations specific to the algorithm they are meant to apply. They are not versatile and can't be used for other algorithms. So an ASIC miner for the SHA-256 algorithm would be unable to mine a blockchain that uses the Scrypt algorithm, such as Litecoin and Dogecoin. They would be less efficient because the Scrypt algorithm is designed to be memory-bound, and ASICs are optimized for calculations, not for memory.
Why Mine With ASICs?
ASICs (Application-Specific Integrated Circuits) are specialized hardware devices designed to perform the calculations needed to mine a specific cryptocurrency efficiently. These devices are designed to be highly efficient at performing the mathematical operations required to solve the complex mathematical puzzles necessary to create new blocks and add them to a blockchain.
One of the main reasons to mine with ASICs is that they can perform these calculations much faster and more efficiently than general-purpose computers. This is because ASICs are designed with specific circuits and logic optimized for the calculations needed to mine a specific algorithm.
Another reason is that ASICs consume less energy per unit of computation than general-purpose computers, making them more energy efficient. This is important because the energy costs of mining can be high, and ASICs can save miners a lot of money in the long run.
Additionally, using specialized hardware like ASICs increases the overall security of the blockchain network, as ASICs are difficult and costly for attackers to acquire and use in their attacks.
It is worth noting that while ASICs can offer significant advantages over general-purpose computers, they also have some drawbacks, such as the high costs of purchasing and operating the hardware. Additionally, ASICs can quickly become obsolete, making them a poor long-term investment.
Mining: SHA256 vs. Scrypt Block Subsidy Rewards
SHA256 and Scrypt miners will experience the halvings equally in terms of the reduced block subsidies from mining Bitcoin and Litecoin respectively. However, Scrypt miners also have the benefit of the constant tail emission from mining Dogecoin, which provides a steady stream of new coins and helps to offset the reduction in block subsidies from Litecoin. This means that Scrypt miners may have a slightly more stable revenue stream compared to SHA256 miners, who rely solely on block subsidies and transaction fees from mining Bitcoin.
How has having the majority of CPU power changed since ASICs?
Before the introduction of Application-Specific Integrated Circuits (ASICs), Bitcoin mining was primarily done using Central Processing Units (CPUs) and later Graphic Processing Units (GPUs). However, ASICs, hardware devices designed specifically for mining certain cryptocurrencies, are far more efficient than CPUs and GPUs. This has led to a massive increase in the computational power of the Bitcoin network but has also resulted in a concentration of mining power, as those who can afford more powerful and numerous ASICs control more of the network's power.
Why can't we compare the CPU power of Scrypt (Litecoin) and SHA256 (Bitcoin) now that there are ASICs?
Scrypt and SHA-256 are different cryptographic hash functions used in Litecoin and Bitcoin. Scrypt was initially chosen for Litecoin to resist the kind of hardware used for Bitcoin, namely ASICs, to allow mining to be more accessible to individuals with regular computers. However, ASICs have since been developed for Scrypt as well.
The difficulty and the hash rate (the speed at which a miner completes an operation in the cryptocurrency code) vary greatly between Scrypt and SHA-256 mining due to the intrinsic complexity of the different algorithms and the technology used to mine.
Hence, it is not fair to directly compare the raw CPU power used for SHA-256 (Bitcoin) mining to that used for Scrypt (Litecoin) mining. They each require different types and amounts of memory and computing resources. Additionally, the efficiency of mining is also heavily influenced by factors like the mining hardware's design and the electricity cost, which can vary significantly between different miners and locations.